Nowadays, it is essential to secure software development. Security risks are everywhere on the net and can affect everyone, not only corporations or government. It is very important to stay aware of the problem.
In this article, you can find informations about the most common security risks and a few tips on how to protect yourself against them.
What is software security?
Software security involves implementing mechanisms during the construction of software to make it functional and resistant to attacks. The goal is to ensure that software remains secure without the need for additional security elements. This is achieved through software security testing before the software is released to the market, evaluating its ability to withstand malicious attacks. It is crucial to integrate security measures from the beginning, avoiding adding extra layers later, although this is sometimes necessary. Users must also be educated on using the software correctly to prevent vulnerabilities.
Secure software development, often associated with DevSecOps, is a methodology that integrates security into every phase of the software development life cycle (SDLC). Security is embedded in the code from the start, rather than being addressed after testing reveals flaws. This approach counters the traditional view that security impedes innovation, causing delays in product release. Considering security during the planning phase is essential, as fixing bugs during implementation and testing is more costly than addressing them during design.
What are the most common security risks?
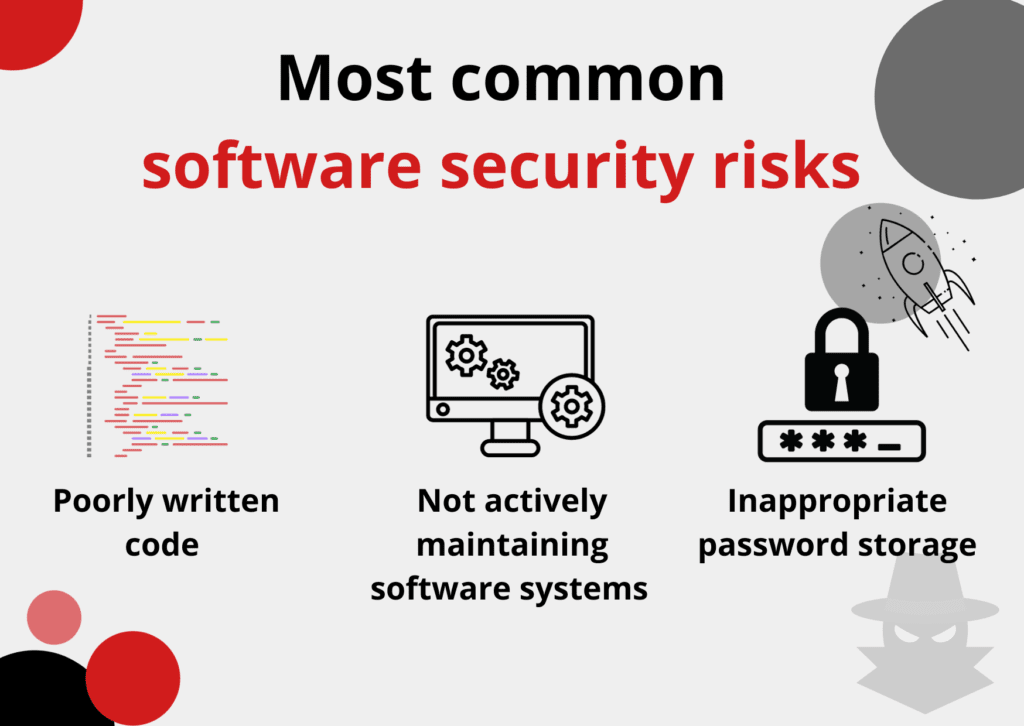
It is worth knowing what is the most common security risk that developers can face.
The first of them is poorly written code. From the beginning of producing the app, it might be not well prepared to safely start. Securing an application becomes difficult when the code is poorly written, and frequently, essential coding practices like input validation, output encoding, error handling, secure storage, and other secure coding practices are neglected.
The second one is a situation in which software systems are not actively maintained, which might lead to vulnerabilities. In that case, if vulnerabilities get exploited once, the hackers the hackers might access secure data and confidential information stored on your server leading to various security issues.
Another one is inappropriate password storage. It is a really common situation that passwords are stored in a way that is really easy for hackers to steal and decrypt them by using various techniques such as dictionary attacks and brute force attacks.
How to protect your software development?
A diverse range of software security tools and solutions are available. Like any other security practice, it’s crucial to formulate a strategy to ensure that your software security solutions remain effective and advantageous.
- Maintaining up-to-date and patched software is essential. Every software may encounter issues, making regular patching a common and vital step in bolstering software security. Utilizing software security services and tools aids in effectively managing the maintenance and inventory of various software programs.
- Adhering to the principle of least privilege involves granting software users only the minimum access required to fulfill their tasks. This means restricting access to features, rights, and controls that are unnecessary. Enforcing a least privilege policy reduces the risk of attacks by preventing inadvertent changes to access rights and unnecessary access to information. Regularly reassessing privileges during employee transitions, project completions, and departures is crucial.
- Automation plays a key role, especially for large companies, in handling the multitude of tasks required for computer security. Automating tasks such as security configurations and firewall analysis requires investment in suitable software security tools.
- Education is integral to mitigating software security risks. Regularly scheduled sessions to educate employees on security risks, the importance of safeguarding information, and actions they can take to enhance personal and company safety. Training should also cover the recognition of security attacks and phishing attempts.
- While no plan can guarantee 100% security, having a software security plan is critical. This plan outlines how the company will operate in the event of a breach, including detection methods and damage mitigation strategies
- Documentation, monitoring, and measurement are crucial aspects of software security. Document all software security policies for easy access and understanding. Over time, monitor and measure activities to ensure users adhere to computer security practices and avoid misuse of privileges. Defining key metrics allows for the tracking of software security risks and improvements over time.
The process of secure software development is an ongoing journey that never concludes. Consequently, it is imperative to consistently seek novel methods to enhance and fortify your code against evolving technology and emerging attack vectors exploited by hackers against software vulnerabilities.
For more interesting and useful insights about startups, visit our blog for articles. In your free time listen to compelling podcasts featuring our clients!
